
First generation languages (or 1GLs) are programming languages that employ machine code. The languages vary with the brand and model of the CPU.
Because coding in machine language is spectacularly tedious and awful, early computer scientists devised an easier way of creating machine code. For a given make and model of CPU, they would create a language that was easier to use than machine code,and then create a set of instructions that would translate programs written in that language into machine code. These languages are considered second generation languages (2GL's).
In early days, this process was thought of as a way to assemble machine code, and the higher level and easier-to-understand languages were called assembly languages. The program (written in machine code) that translated the assembly language to machine code was called an assembler.
Assembly language is said to be a higher level language than machine code, but today, in the context of modern computer languages, is considered to be a lower level language. Most programmers will never have to deal with machine code if they don't want to.
Second generation languages were still quite tedious, and machine-specific. A program written for an IBM computer would absolutely not run on a UNIVAC computer (an early US brand) or a Zuse computer (an early German brand) or a Ferranti computer (an early British brand; yes, British, despite the name). Re-writing a program for another type of computer was almost as difficult as writing it from scratch.
Therefore, computer scientists devised an easier way of creating machine code. They created languages that were easier to write and understand than assembly language, and which automated many operations, reducing the amount of coding necessary in assembly language by about 95%. These languages were called third generation languages (3GL's), and early ones included FORTRAN, COBOL and Basic.
These languages also had to be translated into machine language, and the process of performing the translation became known as compiling the code. The programs that perform the translations are known as compilers.
As wonderful as 3GL's are, they still require significant training and experience to use successfully. Therefore, computer scientists theorized that the next step in programming languages would be ones that (a) were closer in style to natural, conversational language, and (b) allowed the programmer to focus on what needed to be done (function), rather than the step-by-step procedures (process) involved to perform the task. This concept became known as fourth generation languages (4GL's).
In point of fact, there are no generally useful 4GL's. SQL, the standardized software query language that originated in the 1970's and is still used universally to access, manipulate and analyze data in relational databases, was intended to be a 4GL, but falls short of the goals. While it does include many features that allow programmers to focus on function rather than process, it utterly fails at being remotely like natural, conversational language. (Enterprises and individuals spend literally billions of dollars each year on SQL training; obviously, it's not all that natural and conversational.)
Computer scientists have theorized that it would be useful if there were a programming language and model in which programs were written by providing the problem and logic and/or properties of a solution, and allowing the language to create the solution. Such languages are called fifth generation languages (5GL's). So far, despite much work (especially in the 1980s and 1990s), 5GL's have been shown to be impractical for almost everything.
In English, abstraction is the act of representing essential features without including the background details or explanations. In object-oriented programming, abstraction is used to reduce complexity and allow efficient design and implementation of complex software systems.
Abstraction is applied in the process of identifying software objects to model the problem domain. It is the process of reducing these objects to their essence such that only the necessary elements are represented. Abstraction defines an object in terms of its properties, functionality, and interface (means of communicating with other objects).
In the context of computer science, account management is the process of handling and controlling policies and processes that determine who has user accounts on systems and software platforms. It is important that policies be carefully analyzed, considered, devised and enforced.
Active Directory (AD) is a Microsoft technology used to manage computers and other devices on a network. It is a primary feature of Windows Server, an operating system that runs both local and Internet-based servers.
Active Directory allows network administrators to create and manage domains, users, and objects within a network. For example, an admin can create a group of users and give them specific access privileges to certain directories on the server. As a network grows, Active Directory provides a way to organize a large number of users into logical groups and subgroups, while providing access control at each level.
The Active Directory structure includes three main tiers: 1) domains, 2) trees, and 3) forests. Several objects (users or devices) that all use the same database may be grouped in to a single domain. Multiple domains can be combined into a single group called a tree. Multiple trees may be grouped into a collection called a forest. Each one of these levels can be assigned specific access rights and communication privileges.
Active Directory provides several different services, which fall under the umbrella of "Active Directory Domain Services," or AD DS. These services include Domain Services, Certificate Services, Lightweight Directory Services, Directory Federation Services, and Rights Management.
An algorithm is a procedure that is followed to perform a task. While some algorithms are simple, others are quite complex, and programmers may need to spend significantly more time devising or finding an algorithm than writing the code that executes the algorithm. A simple example would be an algorithm to count from 1 to 10 (expressed in pseudo-code):
Step 1: Program starts
Step 2: Store the number 1 as x.
Step 3: Check to see if x is greater than 10; if so, go to Step 7
Step 4: Print the value of x
Step 5: Add 1 to x
Step 6: Go back to Step 3.
Step 7: Program ends
A more complicated example: if one writes a program that draws graphical images, one must perform a lot of calculations to determine which points in the image fall inside various shapes, such as rectangles, and then issue commands to color each point. Fortunately, the modern programmer does not need to deal with such tedious algorithms, because programming languages and libraries provide built-in functions to perform this sort of thing. As recently as the 1980s, almost all programmers had to deal with such long, complex and tedious algorithms.
These days, there are vast libraries of algorithms available to mathematicians and programmers at places like The Computational Geometry Algorithms Library (https://www.cgal.org/).
Most programs involve the storage and manipulation of numbers and text. Because these numeric and textual values often change as the program runs, and may differ each time the program runs, programming languages provide mechanisms to refer to these values using variables, constants, and other storage types.
The program must also set aside, or allocate, the memory that is necessary to store this information. Some languages allocate memory automatically when a variable is first used, and other requires the programmer to first announce its existence by declaring it.
Before any programming can begin, the programmer must understand exactly what it is they are expected to accomplish. They need a target. They must know what the program is required to do, who is going to use it, how the program will receive input, and what output is expected. They must know if there are any special requirements, such as whether it has to operate at a certain speed, or if the program will be dealing with massive amounts of data, whether a network will be involved, what security concerns exist, and so on.
All these criteria must be established before the coding begins, and the collection of this information begins during the analysis and requirements gathering phase.
The American National Standards Institute is a 501(c)3 private, not-for-profit organization founded in 1918. Its stated mission is, "To enhance both the global competitiveness of U.S. business and the U.S. quality of life by promoting and facilitating voluntary consensus standards and conformity assessment systems, and safeguarding their integrity." The Institute oversees the creation, promulgation and use of thousands of norms and guidelines that directly impact businesses in nearly every sector: from acoustical devices to construction equipment, from dairy and livestock production to energy distribution, and many more. ANSI is also actively engaged in accreditation: assessing the competence of organizations determining conformance to standards.
An application programming interface is a set of carefully defined, language-specific keywords, commands, functions, and rules, as well as libraries and compilers, that enable a programmer to write programs in a given language.
Arithmetic operators, such as +, -, *, and /, perform arithmetic functions. For example:
|
EXAMPLE |
EXPLANATION |
|
x = y + z; |
In the C programming language, this adds the values stored in
the variables y and z, and stores the sum in the variable x. The equal sign is an assignment operator, and the plus sign
is an arithmetic operator. |
|
aNum = bNum * cNum; |
In the C programming language, this multiplies the values stored
in the variables bNum and cNum, and stores the product in the
variable aNum. The equal sign is an
assignment operator, and the plus
sign is as arithmetic operator. |
An array is a data structure that consists of variables, or pieces of information, each of which can be accessed by its own array index or key. Arrays provide a handy ways to organize and store large amounts of group information in nearly any common programming language.
ASCII is the acronym for the American Standard Code for Information Interchange. This is the old
encoding standard for use with computers by which each letter, digit, or symbol
is assigned a unique numeric value that applies across different platforms and
programs. ASCII has been superseded by Unicode; technically, Unicode
is a superset of ASCII.
See 2GLs.
An assignment operator, such as the equal sign, causes the corresponding values to be stored in the specified variable; it assigns that value to that memory location. For example:
|
EXAMPLE |
EXPLANATION |
|
x = y + z; |
In the C programming language, this adds the values stored in
the variables y and z, and stores the sum in the variable x. The equal sign is an assignment operator, and the plus sign
is an arithmetic operator. |
|
aNum = bNum * cNum; |
In the C programming language, this multiplies the values stored
in the variables bNum and cNum, and stores the product in the
variable aNum. The equal sign is an
assignment operator, and the plus
sign is as arithmetic operator. |
In HTML, an attribute is a code that is used to provide additional information about HTML elements. Attributes usually come in name/value pairs like: name="value".
Microsoft describes Azure is their "ever-expanding set of cloud services to help your organization meet your business challenges. It's the freedom to build, manage, and deploy applications on a massive, global network using your favorite tools and frameworks."
A web beacon is a tiny graphic image that is used to survey a user's web activity. A web beacon is often a 1x1-pixel image in an email or a website. When a user visits a website or sends an email that contains a web beacon, that information is recorded for analytical purposes. The web beacon may also point to a website by way of the HTML code, thus capturing the web beacon image. The user's IP address is then recorded, as well as how long a particular page was viewed and the time at which it was viewed. Email marketers web beacons to analyze who is clicking on what emails and to collect other email tracking details.
A benchmark is a standard or point of reference against which things may be compared or assessed. When assessing the speed of a program or system, it is useful for programmers to develop benchmarks so they can assess performance advantages and disadvantages of various systems and coding practices. Programmers often employ and/or develop benchmarks, and can learn much by doing so.
Ideally, when one compares such things as the speed of a computer, or a database, or a language compiler, a generally accepted benchmark would be of great utility. As a practical matter, such public benchmarks often are not so useful. One source will compare system A to system B by measuring things Q, R and S, while another source will compare system A to system B by measuring things Q, N and 22, and even thing Q will have a different definition. So while private benchmarks, rigorously and consistently applied, can be useful, public benchmarks are often of limited utility to anyone.
The CPU actually does all its mathematical operations at the bitwise (Base 2) level, which is the fastest way to perform such operations. In the past, it was sometimes convenient for programmers to also work at that level to optimize performance. Also, for the manipulation of certain types of data, such as images, and to perform certain scientific calculations, it is sometimes necessary and/or convenient to work at the bitwise level. (To be honest, in most modern computing, there is little call for the average programmer to be manipulating the individual bits.) For such cases, some languages offer bitwise operators, which provide an easy way to combine and manipulate bits. The common bitwise operators are below. If and when you need to use these, you'll know what these terms mean.
|
& |
Bitwise AND |
|
| |
Bitwise OR |
|
^ |
Bitwise XOR |
|
~ |
Bitwise complement |
|
<< |
Shift left |
|
>> |
Shift right |
A Boolean data type, named for 19th century mathematician George Boole, is useful as a place to store values for which there are only two possibilities, such as yes or no, true or false, or 0 or 1. Although you can also store Boolean values in integers or floats, it is often preferable to store them in a Boolean data type so any erroneous coding that attempts to store non-Boolean values in a Boolean data type causes an identifiable error when you compile or interpret the program.
See switch statement.
In programming, a character is a single visual object used to represent text, numbers, or symbols. These include numerals, alphanumeric values, and symbols such as: ? - + #
Most languages have a storage type that is useful for the storage of characters. In the C programming language, that would be a char (character) data type.
Chrome OS is a Linux kernel-based operating system designed by Google. It is derived from the free software Chromium OS and uses the Google Chrome web browser as its principal user interface. As a result, Chrome OS primarily supports web applications. However, it also lets you:
In most object-oriented languages, a class is a template (model) for creating user-defined objects. To create a new type of object, one first defines its class, which is a template that defines its characteristics, and which consists of definitions of its properties and methods. Then one creates instances of the class, and manipulates those instances in a program.
Any program that communicates with other computers and/or programs to do its job is performing distributed programming. One type of distributed programming is client-server programming. In client/server programming, the workload is divided between two computers and/or programs. The user sits at the client computer and runs the client program, whose purpose is to provide the user interface and make requests of the server. The server, which is typically in another location, responds to requests and sends back information as necessary. So, for example, 100 bank tellers may be running a given client program on 100 different PCs, each of which is making requests of and getting answers from the same server, which is in some faraway location.
Content Management System; a software system that manages the creation and modification of digital content, especially web sites and pages.
To create a computer program, one must build a set of instructions that can subsequently be interpreted by the computer. Computer programming is the process of creating such a set of instructions. The writing of such instructions involves the use of computer code, specific words and symbols that have strictly defined meanings. Therefore, computer programming is also referred to as coding.
In computer programming, it is often useful to include textual explanations or annotations in the source code to make the code easier for people to understand when they later encounter it. Such explanations are called comments or remarks, and are mostly ignored by compilers and interpreters. The syntax for comments varies from language to language.
Many programs exchange information with other programs, or with older versions of the program itself. Programs that can exchange information and cooperate with one another are said to be compatible. During the design phase, requirements with regard to compatibility must be established.
Computer languages must be translated from a human-readable language such as C++ or BASIC into a set of instructions that is in a format the computer hardware can understand and execute. A compiler is a program that performs such a translation. The code that is to be compiled is called source code, and the resulting program, that can then be tested and run, is called the executable image. In some cases, programs are interpreted rather than compiled.
For compiled programs, there are two distinct types of errors: those that become evident when a program is compiled, and those that only become evident when the program runs. The former are called compile time errors and the latter are called runtime errors.
When a compile time error occurs, it means that there is a serious problem, and the compilation did not complete. One cannot subsequently run the program to see what happened, because no executable image was created because of the error. (There are also compile time warnings, which notify us that there is something that is imperfect and ought to be addressed, but allow the complier to complete its task and create an executable image.)
A complex number is a combination of a real number and an imaginary number.
An imaginary number is a number which, when squared, is a negative number. Obviously, such numbers don't exist, and are therefore called imaginary. However, the concept turns out to be useful in advanced physics, so for certain purposes, we accept that they exist.
CompTIA (originally Computing Technology Industry Association) bills itself as "the world's leading tech association... a thought leader and an action leader." They sell certifications, the idea being that people who pass the certification tests know something.
The basic certification is A+. An A+ certification suggests you can identify computer hardware, install and support Windows, troubleshoot software and a little hardware, and know something about security and networks.
Computer management is, in general, the task of managing, maintaining and monitoring computer hardware and software. Also:
This word means join, and as far as I can tell, is used exclusively in the computer world to make ordinary humans feel stupid.
Conditional statements, such the if statement, used in conjunction with relational operators, provide one way to compare values, and thus to let the program make decisions based on conditions. Conditional operators provide similar functionality, but involve the use of different symbols and syntax. The use of conditional operators sometimes lets the programmer create decision-making code that requires a lot less typing than convention if-then-else statements. This example uses the C programming language:
|
EXAMPLE |
OUTPUT |
EXPLANATION |
|
#include <stdio.h> void main() { |
|
|
|
float g = 8; float h = 1; float i = g * h; float j = 50; |
|
We
declare the variable g and assign it the value 8. We
declare the variable h and assign it the value 1. We
declare the variable i and assign it the product of the g * h, or 8 * 1,
which is 8. We
declare the variable j and assign it the value 50. |
|
if (i > j) { printf("%.2f * %.2f is greater than %.2f\n", g, h, j); } else { printf("%.2f * %.2f
is less than %.2f\n", g, h, j); } |
8.00 * 1.00 is less than 50.00 |
Here,
an if statement is followed by an else statement, so if i is greater than j, we print a message that says so, and if i is less than j, we
print a different message that says so. In this example, 8 is less than 50,
so we print the second message. |
|
(i > j) ? printf("%.2f * %.2f is greater than %.2f\n", g, h, j): printf("%.2f *
%.2f is less than %.2f\n", g, h, j); } |
|
This
example uses conditional operators,
in this case a question mark and a colon, to do the same thing, executing a
conditional if-then-else statement. |
A great many programs involve the storage and manipulation of numbers and text. These numeric and textual values often change as the program runs, and may differ each time the program runs, so we must have a general way to refer to them. Also, the program must set aside, or allocate, the memory that is necessary to store this information. Programming languages provide a way to refer to these values, and to allocate the memory that is necessary to store this information, by using variables and constants.
Because it is sometimes convenient to store values in memory locations and assure that the values are not accidentally changed, some languages allowing you to declare and initialize constants for this purpose, and some languages also come with built-in constants.
A programming construct is a syntactically allowable statement of line of code that may be formed from keywords and symbols. Typically, control flow statements are referred to as constructs.
Control flow statements are used to allow a program to make decisions, and to behave differently as conditions warrant. By building such decision-making into a program, we control the flow of the program, thus the phrase control flow. Logically, control flow statement work like this:
If this is the case...
Do this
If this other thing is the case...
Do this other thing
And if neither of those is the case
Do this third thing
There are several types of control flow statements, such as if, switch, foreach and while statements. Their names and syntax vary from language to language.
The CPU or central processing unit is the primary hardware processor for a computer, and performs most of the calculations and control functions of a computer. A CPU is often referred to simply as the processor.
Cascading style sheets are files that contain name/value pairs that determine how HTML elements (such a buttons and menus) will be displayed on screen, on paper or in other media. The files, keywords and the set of rules for their use are loosely referred to as CSS.
The idea is that one creates one or more CSS files, thus setting a bunch of preferences that apply to an entire document or family of documents, and thereby creates and enforces a certain look and feel that is applied to all the documents without having to add a lot of extra code to each document. Thereafter, by changing a single CSS setting, programmers can change the look and feel of the entire family of pages. CSS files can be long and tedious to create, but are nonetheless great work-savers.
(1) Data analysis is the process of systematically applying statistical and/or logical techniques to describe and illustrate, condense and recap, and evaluate data.
(2) In public education, there is a movement towards using data to assess performance of students and teachers on both a macro and micro level, and to apply lessons learned from the analysis to improve performance.
Products like those from Tableau Analytics let educators perform sophisticated education analytics and share their findings. Other important players include SAS (the company takes its named from its original product, which was called Statistical Analysis System) and Panorama Education.
A database is a computer system for efficiently storing, organizing, accessing and changing large amounts of data.
Database design is the process of conceptualizing, arranging, constructing and creating a database. The steps involved are:
Data mining is the process of finding anomalies, patterns and correlations within large data sets to predict outcomes. Using a broad range of techniques, you can use this information to increase revenues, cut costs, improve customer relationships, reduce risks and more. In education, data mining helps us identify and solve problems of which we might very well be unaware.
In programming, a data structure is format and method for organizing and storing values. Usually, the term refers to a general description of a format, and is different from a data type or storage type. For example, an array is a data structure that consists of variables, or pieces of information, each of which can be accessed by its own array index or key. However, depending on the language involved, arrays may be implemented as list storage types or array storage types, or both.
A data structure is not the same things as a structure, which is a specific data type in the C programming language.
See storage type.
To debug is to identify and remove errors from computer hardware or software. While the word is widely thought to have originated in the tale of a moth that caused a malfunction in a computer at Harvard University in the 1940s, the term "bug" has been used to mean "defect" in engineering jargon since at least the 1870s.
There are numerous tools (programs) for debugging, which vary based on the language being used, budgets, enterprises policies, and personal preferences. These are called debuggers.
Some languages require that before a program can use a variable, constant, and other storage type, the program must first announce its existence by declaring it. For example:
|
int x; |
In the C programming language, this statement declares that a variable called x exists, and that it will be used to store integers. |
Declarative programming is a programming paradigm that expresses the logic of a computation without describing its control flow. It dictates what needs to be done, but not how to do it. SQL is an example of a declarative language. Declarative programming languages lack such features as looping constructs.
Functional programming is a type of declarative programming.
See Define.
Different languages have different rules about how variables are created and used. Some languages require that before a program can use a variable, constant, and other storage type, the program must first announce its existence by declaring it. Some languages require that before a program can use a variable, constant, and other storage type, it must be set to some value. To define or initialize a variable is to assign a value to it for the first time. For example:
|
PROGRAM |
EXPLANATION |
|
int x; |
In the C programming language, this statement declares that a variable called x exists, and that it will be used to store integers. |
|
x = 1; |
In the C programming language,
this statement defines or initializes the variable x as 1. |
|
int y = 2; |
In the C programming language,
this statement declares that
a variable called y exists, states that it will be
used to store integers, and defines
or initializes its value to 2. |
|
DIM y as Integer LET y = 2 |
In the BASIC programming language, this statement declares that a variable called y exists, states that it will be used to store integers, and defines it as 2. |
Once the analysis phase of a programming project has been completed, the next step is to design the program. This step involves taking the specifications that were created during the analysis and requirements gathering phase and translating them into a plan that will allow one to build a program that will meet the specifications. This step includes the consideration of such design issues as modularity, portability, compatibility, security, performance and usability. All major design decisions have been made and documented. For example:
DevOps is a loosely defined set of software development practices that combine software development (Dev) and information technology operations (Ops), designed to shorten the systems development life cycle while delivering features, fixes, and updates frequently in close alignment with business objectives. As DevOps is intended to be a cross-functional mode of working, those that practice the methodology use different sets of tools -- referred to as "toolchains" -- rather than a single one. These toolchains are expected to fit into one or more of the following categories, reflective of key aspects of the development and delivery process:
Coding: code development and review, source code management tools, code merging
Building: continuous integration tools, build status
Testing: continuous testing tools that provide quick and timely feedback on business risks
Packaging: artifact repository, application pre-deployment staging
Releasing: change management, release approvals, release automation
Configuring: infrastructure configuration and management, infrastructure as code tools
Monitoring: applications performance monitoring, end-user experience
Any program that communicates with other computers and/or programs to do its job is performing distributed programming.
DomainKeys Identified Mail (DKIM) is an email authentication method designed to detect forged sender addresses in emails (email spoofing), a technique often used in phishing and email spam.
In the context of the WWW, a domain refers to a URL; in the URL http://www.fudgebrownies.us, the domain is fudgebrownies.
In the context of LANs (local area networks), a domain is a collections of objects (users and/or devices) with associated permissions. As used in with LANs, the word goes back at least as far Novell NetWare, which was the first really huge network operating, which made it easy for non-tech companies to network dissimilar computers. (NetWare was originally married to its own Star network hardware, but soon became hardware independent. Eventually, networking standards made the concept of a network operating system obsolete, and NetWare is dead.)
In the context of LANs (local area networks), a domain is a collections of objects (users and/or devices) with associated permissions. As used in with LANs, the word goes back at least as far Novell NetWare, which was the first really huge network operating, which made it easy for non-tech companies to network dissimilar computers. (NetWare was originally married to its own Star network hardware, but soon became hardware independent. Eventually, networking standards made the concept of a network operating system obsolete, and NetWare is dead.)
However, there is still a need for products that make it possible to manage access and security of enterprise computers from a central source, so there are many products like Microsoft Active Directory and LogicMonitor that perform these tasks. This is often referred to as domain management, and refers to the ongoing tasks of keeping a personal or corporate domain (or domains) stable, secure, and able to support related websites.
Basically, domain management is the task of seeing to that data in a domain is secure, and that people have access to the data they need.
Depending upon the language and the manner in which memory is allocated, the data that are stored may be either static (unchangeable) or dynamic (changeable). Also, the memory allocation may be static, in which case memory is reserved for the duration of the program, or dynamic, in which case memory is allocated only as long as it is needed. In general:
A dynamic variable:
When memory allocation is dynamic:
Eclipse is a free, easily available Java IDE that, with the help of plug-ins, is also useful for such languages as Ada, ABAP, C, C++, C#, Clojure, COBOL, D, Erlang, Fortran, Groovy, Haskell, JavaScript, Julia, Lasso, Lua, NATURAL, Perl, PHP, Prolog, Python, R, Ruby, Rust, Scala, and Scheme.
An HTML element is an individual component of an HTML document or web page, such as a paragraph (<p>) or a table (<table>). It typically consists of a tag, some attributes that describe and define it,and the content (text or images) whose appearance is defined.
Encapsulation, in the context of object-oriented programming, refers to an object's ability to hide data and behavior that are not necessary or useful to its user. Encapsulation also enables a group of properties, methods and other members to be considered a single unit or object.
Encapsulation is used to restrict access to the members of a class so as to prevent the user of a given class from manipulating objects in ways that are not intended by the designer. While encapsulation hides the internal implementation of the functionalities of class without affecting the overall functioning of the system, it allows the class to service a request for functionality and add or modify its internal structure (data or methods) to suit changing requirements.
Email Service Provider; a service that enables marketers to send out email marketing campaigns to a list of users.
To make GUIs work, programs must respond to events such a mouse clicks and key clicks that may occur at any time during the execution of a program. This style of programming is referred to as event-driven programming, and relies on the ability of systems, languages and programmers to handle such events. (This term also applies to the creation of device drivers, which are low-level programs that are written and linked into an operating system so that hardware devices such as hard disks, keyboards, DVD players, and speakers work.)
An executable image is file that contains a program that has been converted to low-level instructions by a compiler and is ready to run. Such a program can typically be run by typing its name, or by double-clicking an associated icon.
In programming, an expression is a group of variables or constants, and operators and functions, that are put together in a single statement, and return a value. For example (this is Python code):
|
x = 3 y = 4 z = (x + y) |
Here, (x + y)
is an expression. |
|
print('Union: the union of mySet1
and mySet2: %s' % (sorted(mySet1 | mySet2))) |
|
|
Above, we have several expressions. (mySet1 | mySet2)
is an expression. (sorted(mySet1 | mySet2))) is
an expression. ('Union: the union of mySet1 and
mySet2: %s' % (sorted(mySet1 | mySet2))) is an expression. |
|
A firewall is a part of a computer system or network which is designed to block unauthorized access while permitting outward communication. Firewalls may consist solely of software, or they may need to run on their own hardware. A hardware firewall sits between a router and the internal computer network. Windows has a built-in software firewall. For enterprises that need more than casual security, a more robust and effective firewall is necessary. There are a great many firewall products available.
Fundamentally, numeric vales can be stored in a computer as integers, which have no decimal points, or as a decimals, which are numbers that includes a decimal point. Indeed, some computer languages have a decimal data type.
When storing decimal values, the computer must store not only numbers, but something that indicates where the decimal point goes. Of course, depending on the number in question, the location of the decimal point varies. So it is sensible and convenient to have a data type that stores not only the digits (0-9), and something that indicates whether the number is positive or negative, but also something that indicates where the decimal point goes. The location of the decimal point varies with the value of the number, and is therefore said to float, thus these numbers are called floating point numbers.
Floating point numbers are often stored and expressed using scientific notation.
A for or foreach statement is a control flow statement. Quite often, a program will encounter a list of values, and will need to perform some processing on each member of the list. In this situation, it is useful to repeat the same code several times. Replaying a block of code in this fashion is called looping. The most common and most generally useful looping construct is the for or foreach loop. In the C programming language, they look like this:
|
EXAMPLE |
INPUT/OUTPUT |
EXPLANATION |
|
#include <stdio.h> void main() { |
|
This is an example in the C language. |
|
char
beatles[5][10]={"John","Paul","George",
"Ringo", "Pete"}; |
|
This syntax is a bit complex, but all we are doing is storing
five names in a character array. That array is named beatles, and we can access each member of that
array using the syntax beatles[0]
(for the first member, John), beatles[1]
(for the second member, Paul), and so on. |
|
int i; |
|
We also declare a variable called i, which we will use in the for loop. |
|
for (i=0; i<5; i=i+1) { |
|
Here's the beginning of the for
loop. It has three parts, which are called the initialization, the test,
and the update, often called the increment. The initialization
sets the condition under which the loop will begin. In this case, the
variable i will be set to 0. Each time through the loop, the for statement evaluates the test
statement. If the test condition is true, the loop is executed. If it is not,
the loop is not executed. The first time through the loop, we initialized i to 0, and 0 is less than 5, so we
will execute the loop. The third part, the update,
is a statement that is performed after
the loop is completed. So the first time we run this loop, i is 0, and i is
less than 5, so the loop runs, and if i is used inside the loop, it will have
a value of 0. |
|
printf("%s was a Beatle.\n", beatles[i]); |
John was a Beatle. |
So, the first time through the loop, the message specified by
the printf is printed. i is 0, and beatles[0] contains the word John, so the message John was
a Beatle. is printed. |
|
|
|
Now that that loop is finished, the update is applied, and i
now =i+1,
or 1, |
|
|
Paul was a Beatle. |
Back at the for
statement, the system applies the test, determines that i (1) is less than 5,
and goes through the loop again. This time, since i = 1, we print beatles[1], and will since beatles[1] contains the name Paul, we will see the message Paul
was a Beatle. |
|
|
George was a Beatle. |
i is updated to 2, and we loop through again, and get George was a Beatle, |
|
|
Ringo was a Beatle. |
Ringo was a Beatle, and |
|
} |
Pete was a Beatle. |
Pete was a Beatle.
That last time through, i is updated to 5, so when we do that test, the
system concludes that i is no longer less than 5, and does not execute the
loop again. The brace closes the loop, and |
|
} |
|
the final brace closes the program. |
A programming framework is a complete set of tools that allows a programmer write, compile and run programs. A framework includes an API (a set of carefully defined , language-specific keywords, commands, functions and rules), as well as libraries and compilers. It may also include an IDE.
Programming code is organized into sections that are called routines, subroutines or functions. The precise definition of these terms varies from language to language, and usage tends to be sloppy, but one can generally refer to any reusable piece of code as a routine, subroutine or function.
Functional programming is a style of programming that emphasizes the evaluation of expressions rather than the execution of commands. Functional programming avoids the use of global variables that can be used in common by multiple functions, since changing such a variable in part of a program may have unexpected effects in another part. Functional-style programming is stateless (uses no global variables) whenever possible, in order to avoid incidental side effects. Functional programming is a type of declarative programming.
GIMP is the GNU Image Manipulation Program. It is freely distributed software for such tasks as photo retouching, image composition and image authoring. It works on many operating systems, in many languages.
Git is a distributed version-control system for tracking changes in source code during software development. It is designed for coordinating work among programmers, but it can be used to track changes in any set of files. Its goals include speed, data integrity, and support for distributed, non-linear workflows. Git was created by Linus Torvalds in 2005 for development of the Linux kernel, with other kernel developers contributing to its initial development. The name was chosen by the author with full knowledge of its British meaning (according to the Oxford English Dictionary, "an unpleasant or contemptible person"). See https://github.com/git/git/blob/master/README.md.
GitHub is a web-based hosting service for version control using Git. It is mostly used for computer code. It offers all of the distributed version control and source code management (SCM) functionality of Git as well as adding its own features.
GitHub, owned by Microsoft since 2018, describes itself as "supporting a community where more than 31 million people learn, share, and work together to build software."
The scope of a variable is the part of the program where the variable is accessible. Depending on the rules of a language, a variable can be declared in such a way that it is global, or accessible everywhere in the program, or local, in which case it is only available in a certain part of a program, such as in a subroutine. It is generally useful to limit the scope of a variable so that memory is not allocated at any time other when it is needed. However, it is also sometimes useful to make a variable global, if more than one subroutine will use the value.
A computer's user interface describes the style that is used by users to interact with a computer. In the earliest days of computing, this involved switches on the front panel of the computer. These were replaced by punch cards, which were replaced by alphanumeric keyboards and monitors. By the mid-1990s, the vast majority of computers relied on interfaces that included graphical symbols such as buttons, icons, and menus. These are called graphical user interfaces, or GUIs, and these interfaces are used by virtually everyone today.
Hash tables provide a way to look up records or objects more quickly than might otherwise be possible.
When you have large lists, such as employee records that include name, address, job description, phone numbers, and so on, you typically want to be able to quickly search the list (and subsequently modify records), add to the list, and delete items from the list. This presents certain performance problems. To wit:
Although there are storage and search methods that can improve performance (such as linked lists, balanced binary search trees, and direct access tables), they all have disadvantages. One solution that addresses many of these problems is a hash table.
In a hash table, each individual record is mapped to a much smaller number by a hash function. That smaller number maps to a much smaller list that can be search much more quickly. So what happens is this:
A hashtag is word or phrase preceded by a hash mark (#), used within a social media message or posting to identify a keyword or topic of interest and facilitate a search for it. When a user adds a hashtag to their post, it can be (and usually is) indexed by the social network and becomes searchable and discoverable by other users. Once someone clicks on that hashtag, they are brought to a page that aggregates all of the posts with the same hashtags. Once a keyword picks up enough momentum, it becomes trending.
HyperText Markup Language is the primary language used to create web pages. It is a client-side language that resides on web servers and is interpreted on the client side by web browsers. It is one of the three languages that all web developers need to know:
HTTP is the hypertext transfer protocol, and defines how browsers should interpret HTML pages.
HTTPS is the secure hypertext transfer protocol, and defines how browsers should interpret HTML pages. It works exactly like HTTP, but adds a layer of security by encrypting data that goes to and from the web server.
An if statement is a control flow statement. They allow you to make basic decisions, such as:
|
Explanation |
|
|
if [this condition is met] do this |
A simple if statement causes
something to happen only under a certain condition. It works thus: it applies a test. If the condition is met, the specified action
takes place. If the condition is not met, the specified action does not take
place, and the program continues on to the next line of code. |
|
if [this condition is met] do this else [if the conditions is not met] do this thing |
An if-else statement
causes something to happen only under a certain condition, and causes
something else to happen under all other conditions. It works thus: it applies a test. If the condition is met, the specified action
takes place. If the condition is not met, the specified action does not take
place, but instead, another specified action takes place, and then the
program continues on to the next line of code. |
|
if [this condition is met] do this else if [this other condition is met] do this other thing else if [this third condition is met] do this third thing else [if none of the conditions are met] do this thing |
An if-else-if-else
statement causes something to happen only under a certain condition,
something else to happen under various other conditions, and finally causes
yet another thing to occur if none of the specified conditions are met. It
works thus: it applies a test. If the condition is met, the specified action
takes place. If the condition is not met, another test is applied. If that
condition is met, a specified action takes place. If neither of the
conditions is met, other tests may be applied, each with its own
corresponding actions. Finally, if none of the conditions are met, a final
action takes place, and then the program continues on to the next line of
code. |
An imaginary number is a number which, when squared, is a negative number. Obviously, such numbers don't exist, and are therefore called imaginary. However, the concept turns out to be useful in advanced physics, so for certain purposes, we accept that they exist. A complex number is a combination of a real number and an imaginary number.
Imperative programming is a programming paradigm that uses statements that change a program's state. Imperative programming focuses on describing how a program operates. Languages from FORTRAN to BASIC to C to C++. Procedural and OOP are types of imperative programming.
An implementation is the installation of a given software system on a specific type of computer. For example, a program such as Microsoft Word must be implemented differently on a Macintosh computer that is running the macOS than it would be on a PC that is running Windows, and as a result, the program does not behave identically on the two systems. Likewise, a language compiler must be implemented on different systems, and there may be differences in behaviors of the compiler from system to system.
One implementation issue is that older computers are often 32-bit systems, which means that memory addresses and other data are typically stored in units that are 32 bits (4 bytes) long. Newer computers are usually 64-bit systems, which means that memory addresses and other data are typically stored in units that are 64 bits (8 bytes) long. To the casual user, and usually even to the programmer, this seldom matters, but it occasionally does. For example, a C compiler running on a 32-bit Windows system may allocate 2 bytes for an int, while a compiler running on a 64-bit Linux system may allocate 4 bytes for an int. That means that the limit for how large a number can be stored in an int might vary.
In general, and index is a mechanism for finding information. The index in the back of a book allows us to search for the occurrence of certain words and phrases in the book.
In programming, an index is a mechanism for achieving the same purpose. For example, a last name or a phone number may be used as a key that allows us to quickly access all the information about the person with that last name or telephone number.
In database programming, an index is a data structure that is used by the database engine to help it find and retrieve data more quickly than it otherwise could. In an RDBMS implementation, an index is a copy of selected columns of data from a table and the low-level block addresses of the corresponding data on disk.
In object-oriented programming, inheritance is a mechanism wherein a new class is derived from an existing class, whereby the derived class may inherit or acquire the properties and methods of other classes.
See define.
I/O, or input/output, has several different meanings, but all are related to the notion that computers are involved in accepting user input, such as mouse-clicks and information entered on a keyboard, and providing output, such as answers on a screen or audio.
The plugs on a computer where you can connect keyboards, mice, monitors, speaker, and USB devices are called I/O ports.
In programming, I/O refers to the techniques the program and language use to get input from the user and offer output to the user. In the C language, a function such as scanf can be used to gather input by instructing a program to store information entered on the keyboard in a variable, and a function such as printf can be used to offer output by instructing a program to print information onscreen. In addition, there are number of functions that allow programs and subroutines to share information; one program's output may be another's input.
In procedural programming, an instance is the occurrence of a structure of a certain type.
In object-oriented languages, an instance is the occurrence of an object of a certain class. In most object-oriented languages, when one creates an object,
one first creates a class, which
serves as a template for the object, and includes all its characteristics (attributes and methods). One
then creates an instance of the
object, which is a named occurrence of the object that can be manipulated in a
program in a manner similar to the way a variable is manipulated.
In many computer languages, it is necessary that as you allocate memory by declaring variables, you must also decide how much memory will be set aside for each variable, and how the information will be stored. As always, the terminology varies from language to language, but in general, the storage type determines how the data are stored, and the storage size determines how much space will be reserved for each variable.
The storage type tells the compiler/interpreter how you intend to use the data, and how to store it. For example, if you want to have a variable that will store only positive, whole numbers, in the C language, you'd probably choose to use a the storage type of int, for integer. Doing so tells the system to set aside 2 bytes of storage for each integer, or 16 bits. Of course, the computer actually stores all data as bits -- Base 2 -- and if you think back to the math you learned in grammar school, you'll recall that Base 2 looks like this:
0001Base2 = 1Base10
0010Base2
= 2Base10
0100Base2
= 4Base10
1000Base2
= 8Base10
1010Base2 = 12Base10
That's all based on this, of course:
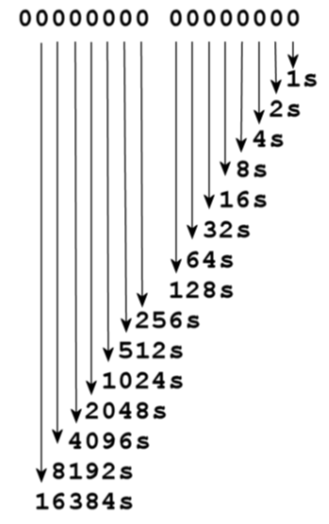
The left-most bit is reserved to designate whether or not the number is a positive or negative number. So, if all the bits are set to 1, then the computer is storing a positive number that is the sum of 1 + 2 + 4 + 8 + 16 + 32 + 64 + 128 + 256 +1024 + 2048 + 4096 + 8192 + 16384, which comes out to 32,767. So a computer can store values from -32,767 to +32,767 in a 16 bit signed integer. If the programmer designates that the number is unsigned, the left-most bit is used to store 215 (2 to the 15th power), or 32,768, and the computer can therefore store from 0 to 65,536, which is the sum of 1 + 2 + 4 + 8 + 16 + 32 + 64 + 128 + 256 +1024 + 2048 + 4096 + 8192 + 16384 + 32768.
Languages provide way to store larger integers by allowing you to specifying the size explicitly. A four byte integer lets you store up to 4,294,967,295, or from -2,147,483,647 to +2,147,483,647. An eight byte integer lets you store numbers from −9,223,372,036,854,775,807, +9,223,372,036,854,775,807, or from 0 to a larger number than I care to write (in scientific notation, it's 1.8446744e+19).
The job of the programmer involves a great many tasks, from design to coding to debugging to maintenance. Programmers, always looking for ways of making their jobs easier, have devised various systems to that end. They developed text editors, like Windows' Notepad, that provided a simple way to enter instructions into a computer. They developed compilers. They devised tools to help them create and print documentation. They developed debuggers, programs that would debug other programs.
As much as these tools were helpful, they were clumsy. A programmer would use one program to write code, but then, to test the program, they had to save the file, close the text editor, invoke the compiler program, wait for the program to compile, and finally run the program. They then might have to go back to the text editor to debug, and perhaps close the text editor and start up a debugger, and then open the editor, edit, save, exit, recompile, wait, re-run, and repeat. It was a grim business.
As early as the 1960s, programmers dreamed of a set of tools that would work together so that a programmer could easily hop back and forth among his tasks, quickly and seamlessly editing, saving, testing, tweaking, re-running, and so on, without constantly opening and closing programs. This concept of a collection of cooperative tools became known as an integrated development environment or IDE.
There were serious technical barriers to IDEs. In particular, most early systems were not well adapted to multi-tasking -- having a single user running several programs at once -- and the alphanumeric monitors of the day made it all but impossible to organize several tasks or programs on the screen.
It was not until 1991 that the first real, effective IDE was born, in the form of the entire Visual Basic programming environment.
The Internet is the global computer network that connects virtually everybody and everything. It runs on the TCP/IP protocol. The world wide web runs over the Internet, but is not the same thing. The Internet is the world wide web and more.
Computer languages must be translated from a human-readable language such as C++ or BASIC into a set of instructions that is in a format the computer hardware can understand and execute. A compiler is a program that performs such a translation. The code that is to be compiled is called source code, and the resulting program, that can then be tested and run, is called the executable image.
In some situations, it is inconvenient that programs need to be compiled. For example, when one creates a web page -- which is indeed a computer program -- that page/program may be accessed on a wide variety of computers which use different operating systems and CPUs. Compiling programs so that they will run on a nearly infinite number of various operating systems and CPUs is all but impossible.
For such cases, there are languages that are interpreted rather than compiled. That is, once the source code for myprogram is written, it is not then compiled so the computer can later run it. Instead, the myprogram source code is interpreted and run by another program -- the interpreter -- when the user invokes (runs) myprogram. A web browser is an example of an interpreter. It interprets web pages when the user opens them.
iOS is the operating system that is used on Apple iPhones.
An IP address is an Internet protocol address. An IP address gives each computer on the Internet a unique identity.These addresses are numbers that conform to TCP/IP standards. Usually, a computer will have two IP addresses, one in the older format that was used until IP version 4 (an IPv4 address), and one in the current version 6 format (IPv6). The older addresses look like this: 66.171.248.169. The newer addresses look like this: 2604:6000:1506:120:7446:1a4b:e8d9:1b63.
The addresses actually consist of two addresses. One identifies your LAN, and the other identifies your address on that network. So if I check my own IP address, I will learn that my PC has an address like 192.168.0.45, but that address is only meaningful to other PCs on the LAN. The rest of the world see me as 66.171.248.169, and a router determines which exact PC is mine. The IPv6 addresses work the same way. The first four numbers (2604:6000:1506:120:7446:1a4b:e8d9:1b63) are the address of your modem or LAN, and the last four numbers(2604:6000:1506:120:7446:1a4b:e8d9:1b63) identify your address on that LAN.
They describe themselves thus: "The ISO is an independent, non-governmental international organization with a membership of 164 national standards bodies. Through its members, it brings together experts to share knowledge and develop voluntary, consensus-based, market relevant International Standards that support innovation and provide solutions to global challenges."
Through 2019, they have developed 22,782 standards for everything from the format of DVDs to an official list of abbreviations for countries. Programmers encounter ISO standards in diverse situations and are usually well served by adhering to them.
The IT Infrastructure Library (ITIL) is a library of volumes describing a framework of best practices for delivering IT services. ITIL is described as a "former acronym," which suggests that while it once stood for something, ITIL now stands for ITIL. ITIL has a certification scheme that takes individuals from Foundation to Master. As a condition for even attempting to take any exam beyond the Foundation level, individuals must complete a course offered by an ATO (Accredited Training Organization).
Java is an object-oriented, general-purpose programming language. It was created in large part to solve the problem that because powerful object-oriented languages like C++ have many implementation dependencies, programs written in such languages often have to be not only recompiled but largely rewritten to run on diverse operating systems. Unlike such languages, Java has as few implementation dependencies as possible, and allows programmers to write programs that can run on any platform without re-coding. Java's goal was to allow programmers to practice the principle of WORA -- write once, run anywhere.
Java accomplishes its goals through the use of Java Virtual Machines. Java is a compiled language, but Java programs are compiled into a bytecode which is identical regardless of the programming operating system and environment in which the programmer works. The files that contain bytecodes can then be executed (run) on any system that has a Java Virtual Machine, the program that interprets the bytecode and runs the program locally, regardless of the underlying computer architecture.
All Java platforms consist of a Java Virtual Machine and an application programming interface (API), which includes a compiler.
To make Java platforms easier to program, more secure, better suited for large enterprises, and to address specific programming challenges, there are numerous software packages that can be used along with Java. These include such packages as JSP's and Servlets, Java Persistence API (JPA), JNDI, JDBC, AJAX, Web Services, Spring and Hibernate.
See Java Platforms
Oracle Corporation, which owns Java, explains that there are four Java platforms, each of which consists of a Java Virtual Machine (VM) and an application programming interface (API). They are:
JavaScript is a programming language that dramatically extends the capability of web pages, mainly by providing mechanisms through which web pages are interactive and dynamic. When a web page does such things as update screen information based on user selections, display animated graphics, and play media, JavaScript is almost certainly at work behind the scenes.
JavaScript is primarily a client-side language, one that resides on the server but is interpreted at runtime by the browser on the client side. However, there are also server-side JavaScript functions that offer certain functionality and performance advantages.
JavaScript is one of the three languages that all web developers need to know:
JavaScript is the same as, or almost the same as, LiveScript,JScript, and ECMAScript. It is an oversimplification to say they are "different names for the same things." See JScript.
See Java
See Java Platforms
See Java Platforms
JScript is a derivative of JavaScript. To be precise, JScript is Microsoft's dialect of the ECMAScript standard (that's the ISO standard for JavaScript) that is used in Microsoft's Internet Explorer. Generally, all JavaScript code works in JScript, but JScript has some features that do not work in JavaScript.
See Java Platforms
See Java
To create a computer program, one must build a set of instructions that can subsequently be interpreted by the computer. Computer programming is the process of creating such a set of instructions.
The instructions must be stored in a manner that is understood by the CPU of the computer. This format is called machine code. However, programming in machine code is tedious and difficult, so there are other systems for creating machine code that are easier than doing it manually. These involved programming languages, which are well-defined, strict sets of rules than can subsequently be converted to machine code by a compiler.
Programming code is organized into sections that are called routines, subroutines or functions. The precise definitions of these terms vary from language to language, and usage tends to be sloppy, but one can generally refer to any reusable piece of code as a routine, subroutine or function.
For convenience, most languages include collections of reusable subroutines so that programmers do not have to constantly rewrite code to perform everyday functions. These collections are called libraries, and sometimes modules. Each language has documentation that describe what functions perform what tasks, and the library in which each function resides.
A list is quite similar to an array, which is a data structure that consists of variables, or pieces of information, each of which can be accessed by its own array index or key. Typically, both arrays and lists can be used to store any data type (floating point numbers, strings, and so on). The biggest difference between is the functions that you can use on them. That is, some built-in routine will work on arrays, some on lists, and some on both. Therefore, it is useful for the programmer to know how a list or array will be processed when they decide whether the data type will be a list or an array.
A local area network is a network of computers that are relatively close together. This contrasts with a wide area network, or WAN, which is a network of computers that are relatively far apart. There is no strict definition for when a network is LAN or a WAN, but typically, computers in a single building or group of adjacent buildings may be part of a LAN, and those separated by greater distances are considered part of a WAN. Usually, different hardware and software technologies are used to connect and secure LANs and WANs.
Logarithms are another way of thinking about exponents. For
example, we know that 24 =
16. Another way of expressing this information is by saying that we need
to multiply 2 by itself 4 times to get 16. This formulation -- looking at it as
how many times do I multiple one number to get to another number--is
called a logarithm. To express a logarithm, I would say:
log2(16) = 4, which
means that to get to 16, I have to multiple 2 by itself four times (2 x 2 x 2 x
2).
Logical operators compare expressions and conclude that the comparison is either true or false. If the expression is evaluated to be true, the operator returns the value 1, and if false, the value 0. There are logical operators for AND, OR and NOT conditions.
Quite often, a program will encounter a list of values, and will need to perform some processing on each member of the list. In this situation, it is useful to repeat the same code several times. Replaying a block of code in this fashion is called looping, and the blocks of code are called loops. See for or foreach statement for an example.
Computers function by executing sets of instructions that are contained in files. Those files must be arranged in a format that the computer understands, and this format is called machine code. Machine code is different for each type of CPU.
In object-oriented languages, a method is a function associated with an object; in some languages, you can also say that a method is a property of an object that is a function.
A modem is a piece of hardware that allows two or more computers to communicate. The name originates with the term modulator/demodulator, dating to the days when modems invariably converted analog signals to digital signals. These days, a household or a business typically has a modem, which communicates with the outside world, and a router, which makes it possible for the modem to communicate with a large number of computing devices on a LAN. Modems and routers are sometimes combined into a single unit.
Programs are often broken down into logical modules, each of which performs a specific task. This both allows many programmers to work on a given project and allows them to create easily re-usable pieces of code. During the design phase, those modules must be defined, and the methods by which they will communicate must be established.
An mx is a mail exchange, essentiallyan email server that both manages email access and tries to filter out spam. Many large and midsize corporations let mx's manage their email, and if the mx decides to block email from a certain mail sender, it may block messages to hundreds or thousands of email addresses, even if the users have no desire for the email messages to be blocked.
An mxgroup is a name given to an mx server. Examples: google.com, barracudanetworks.com, emailsrvr.com, fiatgroup.com, outlook.com, spamhero.com, and so on. There is an infinite number of mxgroups.
A namespace is a mapping from names to objects. A computer file system is a namespace that maps file names to files. Many computer languages organize variables and subroutines in namespaces, and those namespaces (the mappings from name to data) are only valid within some scope; the scope of an object is the region of the program where the name exists and is recognizable; outside of its scope, an object is not recognized or accessible.
We know what a firewall is: a barrier between you and evil.
NAT (Network Address Translation) is a technology used for remapping an IP address space into another one. If you have 200 computers using a single router, that router uses NAT to translate internal IP address to external address. So while your PC may tell you that your IP address is 192.168.0.101 (IPv4) or fe80::28d3:4c7c:2e36:72ac%12 (IPv6), your router translates that into a different address when it is sent to the outside world, and translates it back from the external IP address tot eh internal IP address when the packet returns.
The main purpose of NAT is to limit the number of public IP addresses an organization or company must use, for both economy and security purposes. The security part is this: the NAT process makes sure that only requested and authorized data packets get to your computer. For most private parties, that's all the security you need.
The NIST (known as the NBS until 1988), was founded in 1901, and is a non-regulatory federal agency within the U.S. Department of Commerce. NIST's mission is to promote U.S. innovation and industrial competitiveness by advancing measurement science, standards, and technology in ways that enhance economic security and improve our quality of life. NIST works closely with ANSI on many issues, and government agencies often use NIST standards; they encouraged by law to do so.
Object-oriented programming (OOP) is a programming paradigm in which much of the functionality comes from collections of information called objects. An object is a data type that consists of both data and subroutines that can be applied to data.
As a logical entity, an object typically corresponds to some type of thing that appears in a program, such as a window, or a text box, or an element. As a programmatic entity, an object is a collection of data and behaviors that is given a name. The cool thing about objects, and the thing that sets OOP apart from traditional structured imperative and procedural languages, is that the objects can contain both data (variables) and procedures (methods). OOP is a type of imperative programming.
A critically important piece of software performs and supports the computer's basic functions, providing a way for users to access files and perform tasks. This piece of software is called an operating system. Windows is one operating system, and it runs on most personal computers, as well as many laptops and tablets. macOS is another operating system, which runs on Apple's Mac family of computers. Other operating systems include UNIX, Linux, and Google's Chrome OS. There are also operating systems for smartphones.
Programming languages offer lots of ways that programs can perform logical and mathematical computations, such as arithmetic and comparisons. The symbols used to perform such operations are called operators.
Such operators are combined into expressions. An expression is any permissible (syntactically allowable) combination of symbols that produces a result.
There are several types of operators, including:
Relational or comparative operators
Special operators
A programming paradigm is a model or a general approach to accomplishing a task. These include such approaches as imperative, structured, procedural, object-oriented, declarative, and functional programming.
In general, performance refers to the ability of a program to respond quickly, so users are not kept waiting, and do not become frustrated. During the design phase, the programmer may have to consider performance issues carefully. Not only may a program need to respond quickly, it may be that necessary to write the program in such a way that is uses little memory, so that it can run on older computers, and low-powered tablets and smartphones. Such concerns are considered aspects of the program's performance.
The term platform has no precise definition in computer science, but is used most commonly in one of two ways. (1) It sometime means operating system, as in, "The program was written for macOs, and so does not run on any other platform." (2) It sometimes refers to the software environment in which the programmer works. This may include any or all of these: operating system, programming language, API, framework, and IDE.
A pointer is a variable that stores the memory address of the data to which it refers. This approach has certain advantages over conventional variables.
A variable is a name that is assigned by the programmer, and which refers to a value that is stored in memory. When an executing program refers to a variable, the system must translate the variable name into a memory location before it accesses the corresponding data. This is a perfectly reasonable way to operate, but it does require the system to perform an extra step (the translation) when it accesses data in memory.
Some languages permit a programmer to use a pointer instead of a variable when they wish to do so. A pointer is a variable that stores the memory address of the data to which it refers. By using a pointer, the program avoids the step of having to translate a variable name into a memory location when the program refers to the pointer, which allows the system to more quickly access the data.
In English, polymorphism the ability to appear in many forms. In object-oriented programming, polymorphism refers to the ability to process objects differently depending on their data type or class. More specifically, it is the ability to redefine methods for derived classes. Polymorphism allows one to use a single object for multiple purposes. It allows objects and their methods to behave differently depending on how they are invoked or what data are passed to them.
It is sometimes necessary to create programs that run on more than one operating system. Such programs are said to be portable. During the design phase of a programming project, it must be established whether a given program will be portable, for example, whether it will run only on Windows,or only on a certain version of Linux, or if it will run on some number of operating systems and environments. This issue often influences the determination of what programming language will be used on the project.
Procedural programming is a type of imperative programming in which the program is built from one or more procedures (also termed subroutines or functions). The terms are often used as synonyms, but the use of procedures has a dramatic effect on how imperative programs appear and how they are constructed.
A computer program is a file that contains instructions that cause a computer to perform specific tasks. When a user types the name of the file, or clicks on the name, they cause the program to be started. This is commonly referred to as running a program.
Programs are also called applications or apps. For example, if one instructs a computer that is running the Windows operating system to start the program called Notepad, one can type notes for later reference, and save the notes in a file. Similarly, invoking Word starts word processor (a program designed for the creation of professional-looking documents), and invoking Photoshop starts a program that is useful for editing images.
To create a computer program, one must build a set of instructions that can subsequently be interpreted by the computer. Computer programming is the process of creating such a set of instructions.
In programing, the term properties is commonly used according to its English language definition to refer to the characteristics of one thing or another. In certain languages, however, the term has meanings that are quite specific.
In HTML and CSS, we have attributes, which are values used to provide additional information about HTML elements. Attributes usually come in name/value pairs like: name="value". This association between the name and the value is called a property, although the precise usage of the word varies slightly. In CSS the name in the name/value pair is formally called a property.
In the JavaScript language, objects contain properties, and a property is that same association between a name and a value.
In general usage, a protocol is a set of customs and regulations that apply to a circumstance. In computer programming, a protocol is a set of rules that defines customs and regulations that apply to a specific computing area. For example, TCP/IP, the transmission control protocol/Internet protocol, is a set of rules that defines customs and regulations used to allow computers to communicate on a local area network, wide area network, or over the Internet.
A protocol is not a language, nor is it an API. A given protocol may be implemented using a variety of languages and APIs.
Protocol also has meanings that are specific to certain object-oriented languages.
In many cases, the first step in the coding process is to create pseudo-code. Pseudo-code is an informal, plain-language representation of computer code that illustrates the logic of a program, or part of a program, without bothering with the rules of the language. For example, the pseudo-code for the simple task of multiplying two numbers that are entered by a user might be:
For more complex programming tasks, pseudo-code can greatly simplify the coding process by separating the development of program logic from the development of the code itself.
Random access memory is computer memory -- an electronic processor -- that provides fast access to information. While all computer information is stored on its hard disk, a computer will copy some information to RAM when a given program runs, which makes the programs run much more quickly than they otherwise would. RAM can be endlessly erased and re-used. Usually, programmers need not concern themselves with the low-level function of moving data back and forth from disk to memory, as the operating system handles this for them.
In practical language, a rational number is a number that can be expressed by a fraction. For example:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
(square root of 2) |
|
|
Formally, a rational number is a number that can be in the form p/q where p and q are integers and q is not equal to zero.
Real numbers are the type of number we normally use, such as 1, 15.82, −0.1, 3/4, etc. Real numbers are not imaginary numbers.
Often, programmers find themselves needing to search text strings and text documents for matching words or phrases. One way of searching involves the use of regular expressions. A regular expression is a sequence of characters that define a search pattern. For example, the expression ^doglips can (in some languages) be used to search a text file for any line that begins with the word doglips. The expression colou?r can be used to search for occurrences of either the word color or colour.
The precise syntax and rules of regular expressions vary from language to language.
A database is a computer system for efficiently storing, organizing, accessing and changing large amounts of data. A relational database, or RDB, is a database that organizes data into tables of columns and rows, and provides quick, efficient ways to get at the data. It is said to be relational because the design is derived from an approach that was originally described as a relational model of data. If the term relational database were to be coined today, the system might well be called a tabular (or table-based) database, or TDB.
A database is a computer system for efficiently storing, organizing, accessing and changing large amounts of data. A relational database, or RDB, is a database that organizes data into tables of columns and rows, and provides quick, efficient ways to get at the data. It is said to be relational because the design is derived from an approach that was originally described as a relational model of data. If the term relational database were to be coined today, the system might well be called a tabular (or table-based) database, or TDB.
A relational database management system, or RDBMS, is a system where we store data in tables that are organized logically and functionally, so that we can have quick access to that data. An RDBMS is a full set of languages and tools that allow database programmers and administrators to create, manage, access, modify, and secure the system.
Relational or comparative operators compare values. For example > (the greater than sign) is used to determine if one value is greater than another. a > b tests whether the value of a is greater than the value of b.
Relational operators typically include:
|
> |
greater than |
|
< |
less than |
|
>= |
greater than or equal to |
|
<= |
less than or equal to |
|
== |
equal to |
|
!= |
not equal to |
Relational operators are typically used in conjunction with conditional statements. For example:
|
EXAMPLE |
EXPLANATION |
|
In this snippet of code from a C program, we use a combination of the > (greater than) and < (less than) operators with an if-elseif-else conditional statement. |
|
|
if (age > 64) { printf("You are a senior citizen.\n"); } |
If the user is over 64 years of age, they will see the message, "You are a senior citizen." |
|
else if (age < 21) { printf("You are a minor.\n"); } |
If the user is UNDER 32 years of age, they will see the message, "You are a minor." |
|
else { printf("You are from 21 and 64 years old.\n"); } } |
Otherwise, they will see the message, "You are from 21 and 64 years old." |
See Comments.
Read-only memory is computer memory -- an electronic processor -- that provides fast access to information. However, unlike RAM,ROM is not changeable. A relatively small amount of ROM is found on computers to perform such tasks as initiate the computer start-up. Usually, programmers need not concern themselves with ROM.
A router is a hardware device that connects computing devices such as PCs, printers and computer networks by forwarding packets of data among them. A router often stands between a local group of computers and a modem that is connect to the world wide web, and provides security services. It may act as a firewall.
See function.
For compiled programs, there are
two distinct types of errors: those that become evident when a program is
compiled, and those that only become evident when the program runs. The former
are called compile
time errors and the latter are called runtime errors.
Runtime errors are errors that occur only when the program is run, rather than when it is compiled. They but often more diabolical more difficult to identify than compile time errors, because a program may appear to run properly, yet may produce incorrect results.
In computer science, a sandbox generally refers to an environment where a program runs in such a way that its function are somehow restricted. A program that is sandboxed will not have access to certain hardware or software or data. The precise meaning varies. Here are three types of sandboxes.
(1) A sandbox may refer to a tightly controlled environment where programs can be run, restricting the program can do, giving it just as many permissions as it needs without adding additional permissions that could be abused. A web browser is such a sandboxed program, essentially running web pages you visit in a sandbox. Those web pages that are running in your browser can accessing only a limited set of resources, for example, they can't view your webcam or read your computer's local files without permission. If websites you visit weren't sandboxed and isolated from the rest of your system, visiting a malicious website would be as bad as installing a virus.
(2) In computer security, a sandbox is a security mechanism in which a separate, restricted environment is created and in which certain functions are prohibited. A sandbox is often used when untested code or untrusted programs from third-party sources are being used. Sandboxing refers to when a program is set aside from other programs in a separate environment so that if errors or security issues occur, those issues will not spread to other areas on the computer.
(3) A sandbox is a type of software testing environment that enables the isolated execution of software or programs for independent evaluation, monitoring or testing. In such an environment, a sandbox also may be known as a test server, development server or working directory.
Scientific notation is a way of expressing numbers that are too big or too small to be conveniently written in decimal form. Here's a simple example that uses numbers we can comprehend:
The decimal number 250, which is equal to 2.5 times 102, is expressed in scientific notation as 2.5e2.
The decimal number 0.000250, which is 2.5 times 10-4, is expressed in scientific notation as 2.5e-4.
In computer programming, entities such as variables, subroutines and objects are given names that identify places to store data and programming code. The scope of such entities is the region of the program where the names exist and are recognizable; outside of its scope, such a name is not recognized or accessible.
In the computer world, the notion of security refers to the idea that information needs to be protected from theft, corruption and destruction. The term is also referred to as IT Security and Cyber Security.
There are a great many aspects to computer security. They include:
Security issues must be addressed by programmers during the design phase. Many programs, such as those that allow members of the public to buy and sell on a website, deal with an unknown user at one end and confidential information at the other end. During the design phase, issues related to the security of information must be identified, and the extent to which the program is required to withstand and resist hostile acts must be established.
Search engine optimization is the process of increasing the quality and quantity of website traffic by increasing visibility of a website or a web page to users of web search engines. The term refers to the improvement of results that come about with paying for it; that is, it excludes the purchase of paid placement.
SharePoint is not any one thing. It's a collection of products and technologies under one umbrella name. One does not "know SharePoint" any more than one "knows UNIX" or "knows Microsoft Office." You are likely to know or understand the big picture and basic features of either, but you're much more likely to be an expert only at parts of it.
SharePoint is primarily a server product: it is installed on a server and you connect to it.
You may have some local SharePoint applications installed locally -- such as SharePoint Designer and SharePoint Workspace -- but you may not use them at all. You may connect to and use SharePoint exclusively through a web browser, or through MS Office programs, which work quite well in conjunction with SharePoint.
Microsoft speaks of SharePoint as having six different areas of focus:
Computers function by executing sets of instructions that are contained in files. Those files must be arranged in a format that the computer understands, and this format is called machine code. Because machine code is difficult and tedious to create, most programs are written in a high level language such as C++ or Visual Basic and translated by another program into machine code. The higher level code, written in C++ or Visual Basic or any number of languages, is called source code.
First, SPAMⓒ is a product made by Hormel Foods -- SPiced hAM, or something else, depending whom you ask. In the computer world, the word refers to unwanted email that is sent in large quantities to people who don't want it. No one really knows who first called emails SPAM. It is wrongly believed by some that the name SPAM came from some official acronym in which the P had to do with Pornography. This mistaken belief stems from the name given to the federal law passed in 2003 to combat spam. The CAN-SPAM Act of 2003 was so named when some government employee force-fit the title Controlling the Assault of Non-Solicited Pornography And Marketing onto the bill. But the term SPAM is not really an acronym.
In many languages, there are also numerous operators, beyond the assignment, arithmetic, relational, conditional, logical and bitwise operators, that are useful for various specialized circumstances. A few examples from the C language:
|
Symbol |
Example |
Explanation |
|
+= |
a += b |
Shorthand for a = a + b |
|
*= |
a *= b |
Shorthand for a = a * b |
|
++ |
a++ |
Shorthand for a = a + 1
-- the increment operator |
|
-- |
a-- |
Shorthand for a = a - 1
-- the decrement operator |
A database is a computer system for efficiently storing, organizing, accessing and changing large amounts of data. A relational database, or RDB, is a database that organizes data into tables of columns and rows, and provides quick, efficient ways to get at the data. A relational database management system, or RDBMS, is a system where we store data in tables that are organized logically and functionally, so that we can have quick access to that data. An RDBMS is a full set of languages and tools that allow database programmers and administrators to create, manage, access, modify, and secure the system.
The most widely used language for accessing databases is called SQL, usually pronounced Sequel. (It was originally called SEQUEL, for structured English query language, but the name was quickly changed to SQL because somebody already held a trademark on a product called SEQUEL.)
It is normal to assume that a computer program is just that: a single program that does what it does entirely on its own. Indeed, it is almost always best for the user if an application at least appears to be self-contained. However, with modern computing, it is commonplace for programs to communicate with other programs. Such programs often reside on entirely separate computers that may be close to one another and connected via a local network, or thousands of miles apart and connected by a wide-area network. This allows specialized computers and programs, each designed and optimized to perform a specific task, to execute those tasks, and to share information and functionality not only among computers but among a wide range of users in a great many locations.
Programs that operate entirely on their own use the approach of standalone programming.
Stateless programming is a type of programming in which data storage is transient and independent of everything else. For example, HTTP (the hypertext transfer protocol is stateless. Each request to a web server is executed, but the server stores no data about the request, and does not later recall whether it has executed such a request before. Stateless programming is not ideal for all sorts of programming, since it if often useful for a program to be aware of what has taken place in the past. It is useful both for simple client-server programs and for complex programs that may take advantage of multiple CPUs or threads, and must be careful that one thread does not corrupt another.
In programming languages, a statement is a command that the programmer gives to the computer. For example, in the C language, this statement:
printf("Hello, World!");
causes the program to print the message Hello, World! on the computer screen when the program runs. Of course, statements can get a great deal more complex than that.
Depending upon the language and the manner in which memory is allocated, the data that are stored may be either static (unchangeable) or dynamic (changeable). Also, the memory allocation may be static, in which case memory is reserved for the duration of the program, or dynamic, in which case memory is allocated only as long as it is needed. In general:
A static variable:
When memory allocation is static:
When you choose a storage type such as int, you may, depending on the language involved, either explicitly or implicitly decide how much memory will be set aside for each integer. Languages generally have a default size for each data type, and also have additional keywords available so you can choose the exact size that you need. But, to make matters slightly more confusing, different language implementations may have different defaults values and available values.
Most programs involve the storage and manipulation of numbers and text. Because these numeric and textual values often change as the program runs, and may differ each time the program runs, programming languages provide mechanisms to refer to these values usingnames that are assigned by the programmer, and which refer to values that are stored in memory.
The values may be textual data or numbers that may be integer values, very small decimal numbers or very large floating point numbers. Therefore, languages provide storage types that determine how the values are stored, and how much space is reserved for each value.
The amount of space reserved for each variable depends on the language and the storage type. Character storage types may be stored in memory spaces as small as a single byte, while extremely large numbers may be stored in memory spaces as large as 10 bytes.
A string refers to one or more text characters. "A" is a string. "1h4h$%→" is a string. "A priest, a minister and a rabbi" is a string.
Strong and weak typing has to do not with whether a variable is static or dynamic, but how strict a language is about a data types. A strongly typed language insists that computations be performed with data of the appropriate type, and will produce an error when the program attempts the inappropriate. For example, in Python, a strongly typed language, one will get an error (and the program will exit) if one tries to add an integer and character. On the other hand, a weakly typed language, whether it is static or dynamic, is not so strict about such computations. For example, in C, a weakly typed language, the system will happily add an integer to a character if the programmer tells it to, and will likely return a ridiculous result, but will not generate an error condition.
Structured programming is a programming paradigm that uses statements to change a program's state, focuses on describing how a program operates step-by-step, relies heavily on logical program structure, and organizes programs into logical functions. Structured programming is a type of imperative programming; imperative programs need not be structured.
While arrays or lists provide a mechanism to store many variables of the same type, a few languages also offer structures as a mechanism to store many variables of varying types. This is convenient for certain circumstances, such as one has a similar set of diverse information for each of several things. For example, one might create an employee structure that contains some chars in which a name is stored, some ints in which an employee ID is stored, and other storage types for other information about the employee. Programming libraries may have built-in structures, and programmers may and often do also create their own structures.
In object-oriented languages, structures are mostly supplanted by objects.
See function.
A switch is very much like a router, except that while a router may connect computing devices and networks, a switch connects only computing devices.
A switch statement, sometimes called a case or switch-case statement, is a control flow statement that is available in some languages. When there are several likely possibilities that the program must deal with, a case statement, which is called a switch or switch-case statement in C, is easier to use than a simple if or if-then-else construct, as it requires fewer characters of typing and is easier to read when there are several else if or case conditions. An example:
|
EXAMPLE |
INPUT/OUTPUT |
EXPLANATION |
|
#include <stdio.h> void main() { int
code; |
|
This is an example in the C language. |
|
printf("Enter a legal code: "); |
Enter a legal code: |
A printf statement
invites us to enter a legal code.
This suggests that only certain values are legal, or meaningful. |
|
scanf
("%i", &code); |
41144 |
We enter 41144, and the scanf statement stores that in the variable code. |
|
switch (code) { |
|
We execute a switch.
We'll do something different, depending on what value is stored in the
variable code. |
|
case 22: printf("Code 22:
miscellaneous.\n"); break; |
|
If code stores the
number 22, we'll print the message, Code 22:
miscellaneous., and then break out
of the switch. That break is important in C; if we forget the
break, the program will continue executing all the statements it sees until
it encounters a break. So if I had entered a 22, and did not have a break after the case 22 condition, I would see two printf messages, even though
the case 44
condition had not been met. |
|
case 44: printf("Code 44:
sporting goods,
unmentionables.\n"); break; |
|
If code stores the
number 44, we'll print the message, Code
41144: pet supplies, children's
garments, condiments. Again, the break is necessary. |
|
case 41144: printf("Code 41144:
pet supplies, children's garments,
condiments.\n"); break; |
Code 41144: pet supplies, children's garments, condiments. |
If code stores the
number 41144, we'll print the message, Code
41144: pet supplies, children's garments, condiments.
In this example, we entered 41144
above, so we see this message, and then, because of the break, the program exits the switch
statement. |
|
default: printf("Not a legal
value.\n } |
|
If none of the cases is match, we have a default condition, and
we will see the message, Not a legal value. Legal values are: 22, 44 or 41144. The brace closes the switch
statement. |
|
} |
|
And the final brace closes the program. |
Programming consists of telling the system what to do. Programmers tell the system what to do by issuing instructions. The instructions consist of (1) predefined, language-specific words, called keywords, and symbols that are reserved for use by the language, and which have specific meanings, and (2) rules about how those keywords and symbols are used. The rules are called syntax.
TCP/IP is an abbreviation for the Transmission Control Protocol/Internet Protocol, a set of standards that governs communications on LANs, WANs and the Internet. TCP/IP is two separate protocols -- TCP and IP -- but they are almost always used together. The IP Protocol controls how the packets of information are sent out over the networks. The TCP protocol ensures the reliability of data transmissions sent across interconnected networks.
Starting in the late 1970s, the vast majority of computer programming was performed by programmers who sat before a monitor that was capable of displaying only alphanumeric characters. They would type the instructions to create a program, save the program to a file on disk (or, heaven forbid, a tape), and then type a command to compile the program. This is called textual programming.
A thread is a programming mechanism whereby a program can break itself into two or more tasks that run simultaneously. Threads are useful for programs in which a particular resource may become unavailable for a time, because they allow the program to continue processing other information while waiting for the resource to become available. For example, a program that does a lot of reading and writing to/from a disk may be multi-threaded so processing does not wait for I/O to occur unless it needs the information to continue processing.
Threading is usually accomplished through programming libraries that are CPU-specific rather than language-specific.
(1) In programming, a token is the most basic, simple, lowest level or atomic element of a programming language. For example, a token could be a punctuation mark, a keyword, or an operator.
(2) In a token-ring network, a token is a special series of bits that travels around the network. As the token circulates, computers attached to the network can capture it. The token acts like a ticket, enabling its owner to send a message across the network. There is only one token for each network, so there is no possibility that two computers will attempt to transmit messages at the same time.
See storage types.
Unicode is an international encoding standard for use with computers by which each letter, digit, or symbol is assigned a unique numeric value that applies across different platforms and programs. It is governed by the Unicode Consortium, which is ruled by its members. Full members are Adobe, Apple, Facebook, Google, Huawei, Google, IBM, Microsoft, the Ministry of Endowments and Religious Affairs of the Sultanate of Oman, Netflix, Oracle and SAP. Unicode was preceded by the ASCII standard, which is a subset of Unicode, and many programmers still refer to ASCII when they mean Unicode.
URL stands for uniform resource locator, and a URL serves as the address of a resource on the Internet. A URL indicates the location of a resource as well as the protocol used to access it. For example, http://wwfsmd.ytmnd.com/ not only tells us that there is a resource available at the web address wwfsmd.ytmnd.com, but that the protocol used to access it is HTTP, the hypertext transfer protocol. Other commonly protocol include https (secure hypertext transfer protocol) and ftp (file transfer protocol).
Usually, a program must be easy enough to use that those intended to use it will be able to actually do so without training. The degree to which the program is easily usable is referred to as its usability.
Most programs involve the storage and manipulation of numbers and text. These numeric and textual values often change as the program runs, and may differ each time the program runs, so programs must have a general way to refer to them. Also, the program must set aside, or allocate, the memory that is necessary to store this information. Programming languages provide a way to refer to these values, and to allocate the memory that is necessary to store this information, by using variables, constants, and other storage types.
A variable is a name that is assigned by the programmer, and which refers to a value that is stored in memory. The value may change over time. A variable with typically be given a name such as x or ID, and may be quite long, although use of long variable names is poor programming practice because such long names lead to errors.
Visual programming is programming that uses a GUI to allow the programmer to create GUI-based programs by dragging and dropping interface elements such as buttons, windows and menus,then type in whatever code was necessary to label them or make them behave properly. Visual programming still requires some textual programming, but reduces the amount dramatically.
All programming that relies on the world wide web is client-server programming, but very often, more than just a single client and single server is involved. There may be several servers involved, as when one is accessing one's bank account; one's own ISP (Internet service provider) is providing access to the world wide web, while the bank's server is providing access to your account information, and yet another server may be providing access to secure financial information. There may also be multiple clients involved, as when online gamers are competing and chatting. And distributed programming that relies on access to the world wide web, and which use its communication mechanisms, is said to be a web-enabled program.
A while statement is a control flow statement. A while loop works a lot like a for loop, but is syntactically different, and a better choice in some cases. While a for loop runs some pre-determined number of times, a while loop will run until a pre-determined condition is met.
|
EXAMPLE |
OUTPUT |
EXPLANATION |
|
#include <stdio.h> void main() { int hourly = 10; int salary=0; |
|
This example uses the C programming language. It begins with
standard stuff, and the initialization of a 2 variables. |
|
while (salary < 200000) { salary = hourly * 40 * 52; |
|
Each time we go through the while
loop, we calculate the annual salary of a person who earns the specified
hourly rate, assuming that they for 40 hours a week for 52 weeks a year. We
will repeat the loop as long as the salary is less than $200,000 per year. |
|
printf("%i an hour = %i a year.\n", hourly, salary); hourly = hourly + 5; } } |
10 an hour = 20800 a year. 15 an hour = 31200 a year. 20 an hour = 41600 a year. 25 an hour = 52000 a year. 30 an hour = 62400 a year. 35 an hour = 72800 a year. 40 an hour = 83200 a year. 45 an hour = 93600 a year. 50 an hour = 104000 a year. 55 an hour = 114400 a year. 60 an hour = 124800 a year. 65 an hour = 135200 a year. 70 an hour = 145600 a year. 75 an hour = 156000 a year. 80 an hour = 166400 a year. 85 an hour = 176800 a year. 90 an hour = 187200 a year. 95 an hour = 197600 a year. 100 an hour = 208000 a year. |
We print the results of the calculation, and then add $5 to the
hourly rate. The output is as shown. Notice that the final line shows an output for a salary of
$208,000, although the while
condition specifies 200,000. That's because the calculation that changes the
value of salary occurs after the
test is applied. The second-to-last time the while test is applied, the value
of salary is 197,600 when the test
is performed, and only then is it changed to 100 * 40 * 52, or $208,000. The
next time we get to the top of the loop, salary is$208,000, which is not less than 200,000,
so the loop is not executed. |
A wide area network, or WAN, is a network of computers that are relatively far apart. This contrasts with a local area network, or LAN, which is a network of computers that a relatively close together. There is no strict definition for when a network is LAN or a WAN, but typically, computers in a single building or group of adjacent buildings may be part of a LAN, and those separated by greater distances are considered part of a WAN. Usually, different hardware and software technologies are used to connect and secure LANs and WANs.
The world wide web is an information system that runs on the Internet and make information easily available, easy to find, and connected by links. It relies on:
Windows Server refers to a group of operating systems -- all variations of the Windows operating system -- for enterprise-level management, data storage, applications, and communications. It includes all the software on a typical Windows system, and more, including various servers. Windows Server also supports higher end hardware, allowing more memory and more processors.
Copyright© Hands On Technology Transfer, Inc.